Estimator Web License Configuration and Technical FAQ - For IT Admins
Configuring your Active Directory and Conditions Access for web license login in Estimator
Active Directory Activation - IT Department
Our AAD mechanism uses Microsoft Azure B2C and B2B and no credentials are stored in our environment. Any MFA configured by your IT team for your company's identities will factor into this authentication when used.
This process leverages your users' Azure accounts to acquire a license, with all relevant information securely logged into your Azure system. Additionally, our VDI environment is based in the Central Region so user login details will reflect activity from Iowa.
Here are the steps to approve the license to use Active Directory using your Admin Credentials.
1. Adding the DESTINI Single Sign-On to your Environment
- Log in to this website: https://login.beck-technology.com/ and click the Sign-in" button.
- Sign in to Active Directory using your admin email and password, then follow the prompts.
- Once everything is verified you will see the message below
.png?width=670&name=mceclip0%20(2).png)
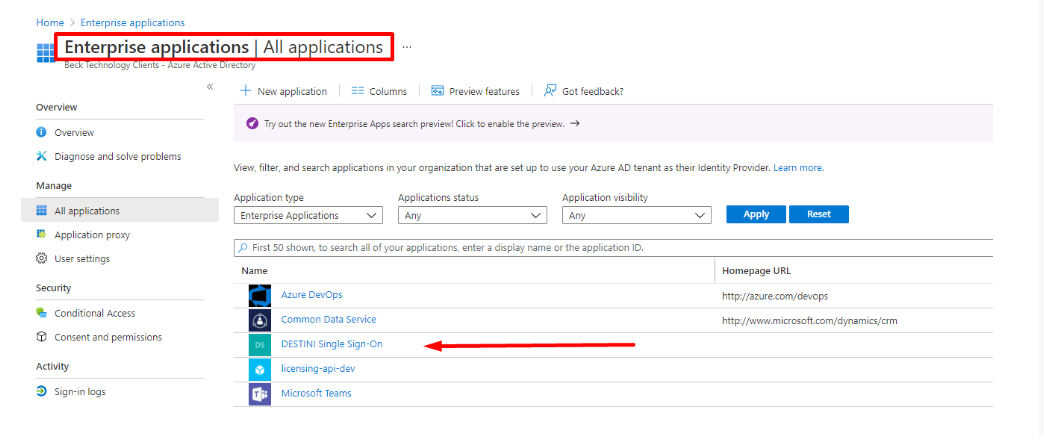
- This will create the DESTINI Single Sign-On in your Azure environment.
- Also, the Azure Administrator may have to go to their Azure Portal > Enterprise Solutions and approve the DESTINI Single Sign-On as well.
Once that is completed then follow the steps below to use your Company's email address to log into our license platform.
If you are getting a security alert accessing the Web License portal, then these are the websites that need to be white-listed. These IP addresses may be dynamic so it would be good to check the IP using the website link.
https://licensing.beck-technology.com/ IP Address - 52.173.149.254
https://becktechauth.b2clogin.com/ IP address - 40.126.29.05 -40.126.29.14
https://login.beck-technology.com/ IP Address - 52.173.149.254
Also, whitelisting IP addresses may not be a feasible solution due to our use of load-balanced Azure Virtual Desktops with Remote App Streaming. This setup results in dynamic changes to the virtual desktop IP addresses, making it challenging to maintain an effective whitelist. Instead, we recommend implementing alternative access control methods, such as user authentication and conditional access policies. These approaches provide a more flexible and secure way to manage access to Active Directory.
Here are some additional recommendations from Microsoft if you are setting up Conditional Access Policies - https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-configure-risk-policies
Estimator Web License Technical FAQ
We use Azure B2C to allow users to sign in to our application by interfacing with web pages hosted by Microsoft. The way we use Azure B2C is to provide authentication, either through user registrations in our own B2C Active Directory or through external Active Directories (i.e., the corporate Active Directories of our customers).
In order to authenticate users from external Active Directories, we have to create a multi-tenant application registry in an Active Directory we control, and register the AD as an identity provider.
The Licensing API is accessed by two different clients:
-
Web portal (using OAuth 2.0 implicit flow )
-
Estimator (using standard OAuth 2.0 access tokens)
Authorization is handled internally by our Licensing AP.
1. How many days can I check out a web license?
Answer - You can only check out a web license for a max of seven days, after that it will automatically check itself back in and you will need to log in to check it out again.
2. How to check out a web license?
Answer - You can only check out a license while you are not in an estimate.

3. Do I have to sign into the license every time I launch the application?
Answer - No, the login is remembered when you first sign in unless you sign out, this token that we can control will last for 14 days before it asks to reauthenticate.
4. If I open another session Estimator, am I using another license?
Answer - No, you will be using the same license tied to your name
5. After checking in my license I get a pop-up message

Answer - This is fine, once you click OK, the license will check back to the server.
6. Why is my license grayed out and cant Check out my license?

Answer - You cannot check out a license when you have an estimate opened.
7. Do I need to be on VPN to get a license?
Answer - No. However, you may need to be on VPN to access your Company's databases
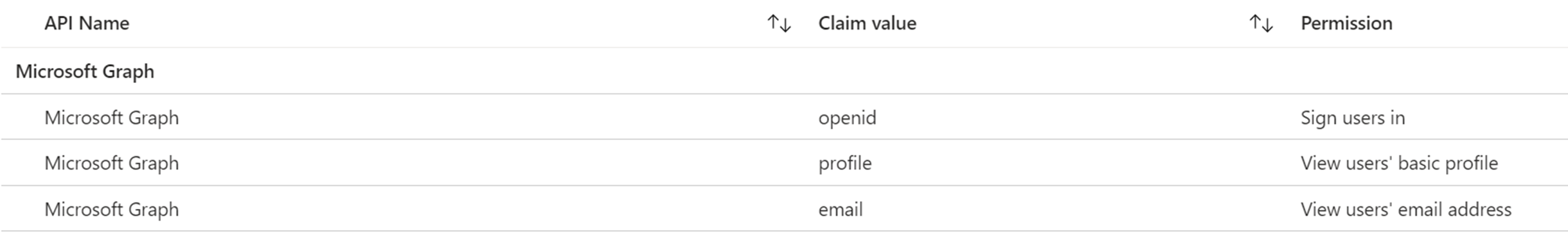
8. Single Sign-On (SSO) - What are the additional permission requested by SSO?

Maintain access to data you have given it access to - This permission is required for single sign-on (SSO) and allows a refresh token to be returned from the authentication flow so that the Azure Web License application can perform task and synchronizations without user involvement and not prompt the user every time their primary authentication token times out.