Hosted DESTINI Applications Architectural Overview and Technical FAQs
Hosted Estimator - Windows Remote Desktop/Windows APP
Here are some FAQs about our hosted environment. If you have additional questions that are not answered below, or need additional clarification, please contact Beck Technology Support.
Functionality
What does the Entity-Relationship Diagram (ERD) look like for Beck Technology's DESTINI hosted model?
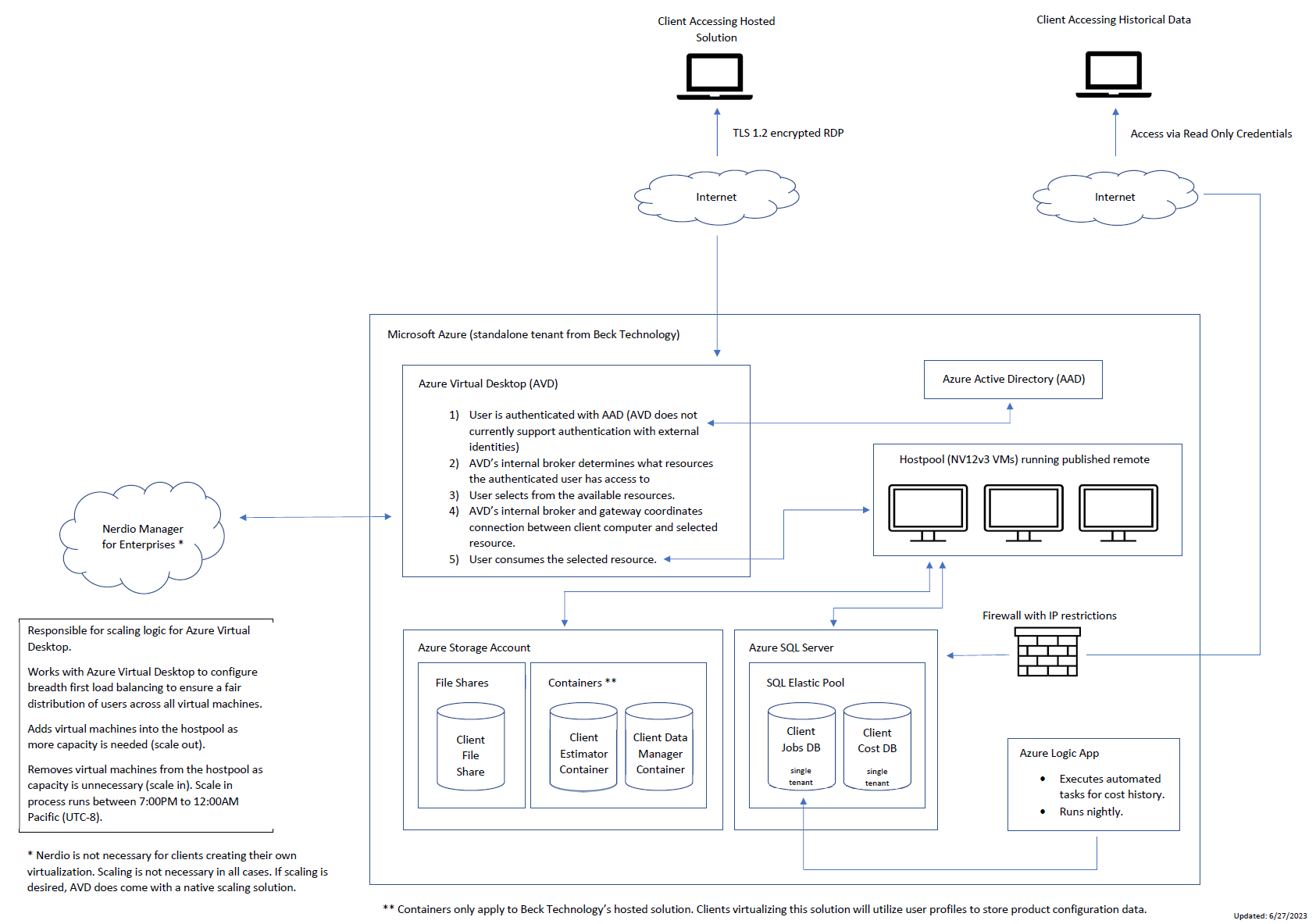
Here are some key notes about this environment:
Location of Severs
- Our applications and SQL servers are hosted in the South Central and Central US regions.
User setup and Application
- DESTINI Estimator - All users will get the app
- Setup and login credentials are sent to the users from Beck Technology Support
- DESTINI Data Manager (Optional) - Only Cost database builders will get the app
BIM360 Docs - 3D Takeoff Integration
- Required BIM360 subscription information can be found here.
- Autodesk Login credentials required
- Cloud Data repository (3D Revit or Navisworks models)
- BIM360 Docs require Forge API enables and will be used for Document Management for 3D QTO (Contact your BIM group Admin or Autodesk Representative for more information on how to enable the Forge API ).
- Estimator ONLY reads the data, it does not make changes to the model.
Procore - 2D Takeoff Integration (Seperate from Estimator 2D takeoff)
- Required Procore subscription from Procore
- Overview of the Procore integration with DESTINI Estimator
- How to set up Procore to use with DESTINI Estimator
Beck Technology Web License
- Users log in from within Estimator using their Company's Active Directory or sign up to log in, info can be found
- How to log into the Web License Platform in Estimator
- Requires IT configuration to use Active Directory
TECHNICAL FAQs
Reliability, Availability, and Uptime
- Is there a way to determine how much outbound and inbound traffic will be encountered on endpoints? Many of the users work from home, and we are concerned about employees using up their personal data while using the hosted DESTINI option.
We do not provide metrics to see actual or estimated bandwidth for individual users of DESTINI Estimator. However, you can use the Remote Desktop Network Guidelines (https://learn.microsoft.com/en-us/windows-server/remote/remote-desktop-services/network-guidance) provided by Microsoft to estimate how much bandwidth may be consumed.
Does Beck Technology offer a way to locally cache data on Clients' endpoints aside from the disconnected workflow and checking out multiple projects?
The solution and its data lives in Microsoft Azure. There is currently no mechanism that allows for a local cache to be made for the ability to work disconnected.
What kind of application reliability, availability, and uptime scores do you offer, especially during times of peak demand Time?
Specific SLA numbers are documented in your contract. As a general rule, we cannot provide SLA numbers that exceed the SLA numbers that Microsoft provides us for the use of their service.
What is the Agreed Service Time (AST) for Beck Technology's hosted DESTINI environment?
DESTINI Estimator is intended to be available 24/7 with the exception of planned maintenance windows. Among other things, unplanned maintenance and Microsoft Azure outages may impact availability of the service.
Beck Technology also provides its standard support hours to all clients and includes phone, email, and community-based support.
What type of monitoring will Beck Technology do to ensure network performance and report uptime, latency, and traffic surges?
We use a collection of technologies within Microsoft Azure and Nerdio Manager for Enterprise to monitor the state of the cloud environment and make adjustments as necessary.
What types of metrics will Beck Technology determine performance or latency?
There are many metrics including VM performance counters, Azure SQL Server and Database metrics, Azure Virtual Desktop telemetry, and others that are used to describe the performance of the cloud solution as a whole. There is no single metric that tells the complete story, and all of this information is used to understand the entire picture.
How will issues with network performance, latency, downtime, and traffic surges in the DESTINI system be communicated to Clients by Beck Technology?
If an unplanned outage occurs, reasonable attempts will be made through email and phone calls to alert main points of contact within a client. Planned outages will be communicated to main points of contact within a client through email. Communicating any infrastructure challenges that don’t result in outages will be considered on a case by case and will be communicated in the same manner as an unplanned outage if needed.
Will Beck Technology scale capacity automatically during traffic surges?
Yes. We use scaling technology to ensure compute is available for demand. As a general process, we scale out during the day as demand increases and limit scaling in operations to off hours. Additional automated or manual scaling may occur on an as needed basis.
What happens when there is a traffic surge that is 10X or 100X the usual traffic, causing the capacity to get used up?
We pre-stage compute to meet the standard start of day surge as users begin their work for the day. To mitigate impacts caused by sudden, large surges, we keep compute on standby for quick access. If the standby compute becomes fully utilized, our scaling technology will continue to scale out and introduce more compute as needed.
Is your auto-scaling reactive (the system reacts to changes but does not anticipate them) or predictive (the system tries to predict future resource requirements in order to ensure sufficient resource is available ahead of time)?
The scaling process is reactive, and it reacts based on rules and thresholds we put in place to ensure compute is available to meet the demand. We analyze usage patterns and configure pre-staging, scaling aggressiveness, standby compute, etc. to ensure the scaling logic is prepared for the demands put on the platform. As a general rule, our scaling strategy is intended to ensure there is always available compute for more users than are concurrently in the platform.
How will Beck Technology handle maintenance both internally (updating or upgrading DESTINI) and externally with Azure? Are the servers set in different availability groups?
Beck Technology will make reasonable efforts to deploy all product updates and Azure-related maintenance during off-peak times to mitigate impact on users. Planned maintenance windows shall be communicated ahead of time.
What type of storage redundancy is being used on the servers?
Beck Technology uses geo-redundancy for Azure SQL databases and Azure storage through paired regions. All data is stored within US based Microsoft Azure regions.
How many data centers does Beck Technology have and what zones are they located in?
DESTINI Estimator is currently deployed to Microsoft’s South Central US Azure region with geo-redundancy data pairing with North Central US.
How many customers are on each server?
Client data is single tenant, and each client has dedicated Azure SQL databases. How users are distributed across the various compute resources varies as we monitor the environment and routinely fine tune load balancing to ensure a performant experience.
Security
What are Beck Technology's security policy and security measures for protecting the data centers and other facilities?
DESTINI Estimator is hosted within Microsoft Azure. Microsoft is responsible for all security policies and security measures for protecting the data centers and other facilities.
What security measures or processes are in place (SSL certificates etc.) to protect sensitive data?
All DESTINI Estimator data is stored single tenant to mitigate cross contamination of data between clients. All data is encrypted at rest. MFA is required on all accounts that access Azure Virtual Desktop to prevent unauthorized access to published apps.
How will Beck Technology protect data from cyber threats, identify malicious IPs or bad bots, and block access?
DESTINI Estimator’s hosted solution is built on top of Azure Virtual Desktop. Azure Virtual Desktop uses a reverse connect method to access the platform. A brief overview of Azure Virtual Desktop connectivity can be found in Microsoft Docs - Understanding Azure Virtual Desktop network connectivity. Accessing Azure Virtual Desktop requires authentication through Azure Active Directory accounts backed by MFA.
For clients needing direct access to their Azure SQL database, firewalls are managed to ensure only office IPs have access to those databases.
We utilize Microsoft Defender for Cloud to monitor traffic, look for oddities, etc. to help ensure the right traffic and access is getting in.
Will any extra security be in place to prevent DDoS attacks?
With DESTINI Estimator being built on Azure Virtual Desktop, DDoS prevention is managed by Microsoft and no additional resources are deployed.
How often will Beck Technology conduct malware/virus scans?
Virtual Machines are configured with 3rd party endpoint protection to provide continuous protection.
Has Beck Technology performed penetration tests on your systems?
With DESTINI Estimator being built on Azure Virtual Desktop, any penetration testing is handled by Microsoft. How will data transmissions be encrypted between Beck Technology's data center and Clients' endpoints when projects are checked out or data is moved between the data center and clients' endpoints?
Azure Virtual Desktop utilizes the RDP protocol and includes TLS 1.2 encryption. A brief overview of Azure Virtual Desktop connectivity can be found in Microsoft Docs - Understanding Azure Virtual Desktop network connectivity.
What data encryption methods will be used? At rest or in transit?
Data is encrypted at rest using Transparent Data Encryption and AES-246. RDP traffic related to Azure Virtual Desktop is also encrypted in transit with TLS 1.2.
What are your terms when it comes to ownership of data?
This is best described under the agreement you signed with Beck Technology.
Who has access to our data in the cloud? Is there a separation of access between roles within Beck Technology? For example, DBAs only have access to the data layer, developers only have access to logic, but not data. Support staff should not have access to data and logic.
We follow a least privilege access methodology for providing access to various types and levels of data, and access is granted based on the roles of individuals within the organization. Most employees at Beck Technology do not have any access to production data or infrastructure.
How will Beck Technology protect and isolate Clients' data within Azure, so Clients' data is separated from other clients' data?
All of DESTINI Estimator’s data is stored single tenant.
Will the Clients' Jobs and Cost database be in a separate resource group?
While all client data is housed single tenant, the underlying nuts and bolts of the Azure infrastructure may change on a regular or semi-regular basis to manage security, performance, etc.
How is Beck Technology partitioning the servers?
While all client data is stored single tenant, the application infrastructure is multi-tenant.
What protocols are in place to prevent users from accessing data on the same server that isn’t part of their partition?
All client data is stored single tenant to prevent cross-contamination of data and data access between clients.
What steps will be taken to stop data leakage from occurring?
All client data is stored single tenant to prevent cross-contamination of data and data access between clients. All client data is protected by unique credentials and connectivity restrictions.
What tests will be performed and conducted to ensure every partition is separated from the other?
All client data is stored single tenant to prevent cross-contamination of data between clients. There are no partitions to test.
How will Beck Technology handle Clients' data as part of a security breach?
This is best described under the agreement you signed with Beck Technology.
How does Beck Technology destroy cloud data? What type of data destruction software will be used? How is physical hardware destruction handled?
DESTINI Estimator data resides in Microsoft Azure. Any data deleted from Microsoft Azure utilizes the delete commands associated with the applicable resources. Any physical hardware destruction is handled at the discretion of Microsoft as they manage their data centers.
Who is responsible for the various security tasks?
Microsoft is responsible for the overall security of its Azure infrastructure.
Beck Technology is responsible for the deployment and maintenance of services and components deployed within Microsoft Azure.
The client is responsible for their users, any hardware, and any non-Microsoft Azure infrastructure the user utilizes.
What is Beck Technology responsible for?
Beck Technology is responsible for monitoring its cloud infrastructure and environment and working with appropriate parties (i.e Microsoft, the client, etc.) to resolve any issues.
What is the Client responsible for?
Working with Beck Technology to resolve any issues that may be directly within the client’s control.
What cloud security certifications does Beck Technology have?
None.
Cloud Security Alliance (CSA) - Certificate of Cloud Security Knowledge (CCSK )
None.
(ISC)2's - Certified Cloud Security Professional (CCSP)
None.
System and Organization Controls 2 (SOC 2) Compliance Certification
None.
Global Science and Technology Forum (GSTF) - Certified Cloud Security Specialist (CCSS)
None.
Cloud Credential Council - Professional Cloud Security Manager
None.
EXIN - Certified Integrator Secure Cloud Services
None.
Cloud Security and Risk Fundamentals
None.
CCNP Cloud/CCNP Security - Cisco Certified Networking Professional (CCNP) – Cloud and Security
None.
Microsoft - Azure Security Engineer Associate
None.
What IP addresses should be whitelisted to avoid false alerts?
AVD is a PaaS. Beck Technology is not exposing any endpoints directly and relies on the AVD and Azure elements of the gateway, broker, etc. to orchestrate everything. Because we're not standing up explicit endpoints, we don't have a specific set of IP addresses or a block that represents our session hosts. Microsoft does document and communicate the IP ranges that AVD has dedicated to it, and all of the negotiated endpoints should come from one of these ranges. To find the ranges specific to AVD, you can search for WindowsVirtualDesktop in the downloaded JSON file from the following link: Download Azure IP Ranges and Service Tags – Public Cloud from Official Microsoft Download Center
Backup and Disaster Recovery
What is your backup policy?
- Azure SQL database backup
- Weekly full backup (schedule is not controllable)
- Daily differential backup (schedule is not controllable)
- Transaction backups every 5-10 minutes (schedule is not controllable)
- Azure SQL database retention (while a client)
- 7-day recovery for a point in time recovery (PITR)
- Full weekly backups kept in long term retention (LTR) for 26 weeks
- Azure SQL database retention (while not a client)
- A full backup is kept in LTR for at least 365 day
- Azure SQL database recovery
- Point-in-time restore as recent as a most recent backup or as old as 7 days.
- Weekly restore points for any period beyond 7 days.
Clients can request a copy of their database for their own backup and retention purposes through our support.
Do you have a disaster recovery plan?
Yes. There is a Disaster Recovery Plan (DRP) for DESTINI Estimator.
How often will Beck Technology test the disaster recovery plan? Best efforts are made to test all or part of the DRP at least once a year.
How resilient is Beck Technology's architecture?
DESTINI Estimator’s Azure Virtual Desktop infrastructure is deployed into a single Microsoft Azure region and makes use of availability zones for certain resources. Data infrastructure employs geo-redundancy to provide data resiliency.
How will hosted DESTINI run if Beck Technology's infrastructure experiences downtime? Is there a method for users to access the data during downtime?
There is no ability to utilize an Azure Virtual Desktop deployed DESTINI Estimator outside of the Azure Virtual Desktop environment. Depending on the nature of the service disruption, our team will work internally and with clients to regain access to the platform.
What will Beck Technology be accountable for in terms of an outage? Will charges be suspended or refunded?
This is best described under the agreement you signed with Beck Technology.
Miscellaneous
Does the vendor provide any mobile apps for this application?
Beck Technology does not provide any specific mobile applications for DESTINI Estimator.
Will this project collect, use, or otherwise process personal data? - Per MIP-91, "Personal Data" means any information that identifies or relates to an identified person and may include a name, a unique identification number, an email or IP address, or other information associated with the individual, such as guest account information, associate personnel information or other data specifically recognized as Personal Data by applicable laws, regulations or legal authorities.
Business user names and email addresses are provided to DESTINI as part of the licensing and authentication process. This information is logged by DESTINI and used for the purpose of communicating who used the system and who performed specific operations against data. Some Azure Virtual Desktop diagnostic telemetry logs IP
addresses for the purpose monitoring and analyzing the Azure Virtual Desktop environment.
Will this project collect, use, or otherwise process sensitive personal data?
No.